WHAT IS ONPAGE
Rise Above the Clutter®
Elevate urgent notifications and facilitate secure team collaboration in critical situations.
Ensure that critical notifications rise above the clutter® and are always received by the right on-call teams.








Elevate urgent notifications and facilitate secure team collaboration in critical situations.
Ensure that critical notifications rise above the clutter® and are always received by the right on-call teams.
Streamline secure collaboration and communication workflows to drive fast incident response times.
Hospitals, SecOps, DevOps, ITOps, supply chain operations and many more, leverage our cutting-edge technology to:
Elevate and automate critical alert management
Reduce communication friction between team members through secure messaging

OnPage is a G2 Leader for incident alert management, consistently receiving recognition for high performance and user satisfaction.
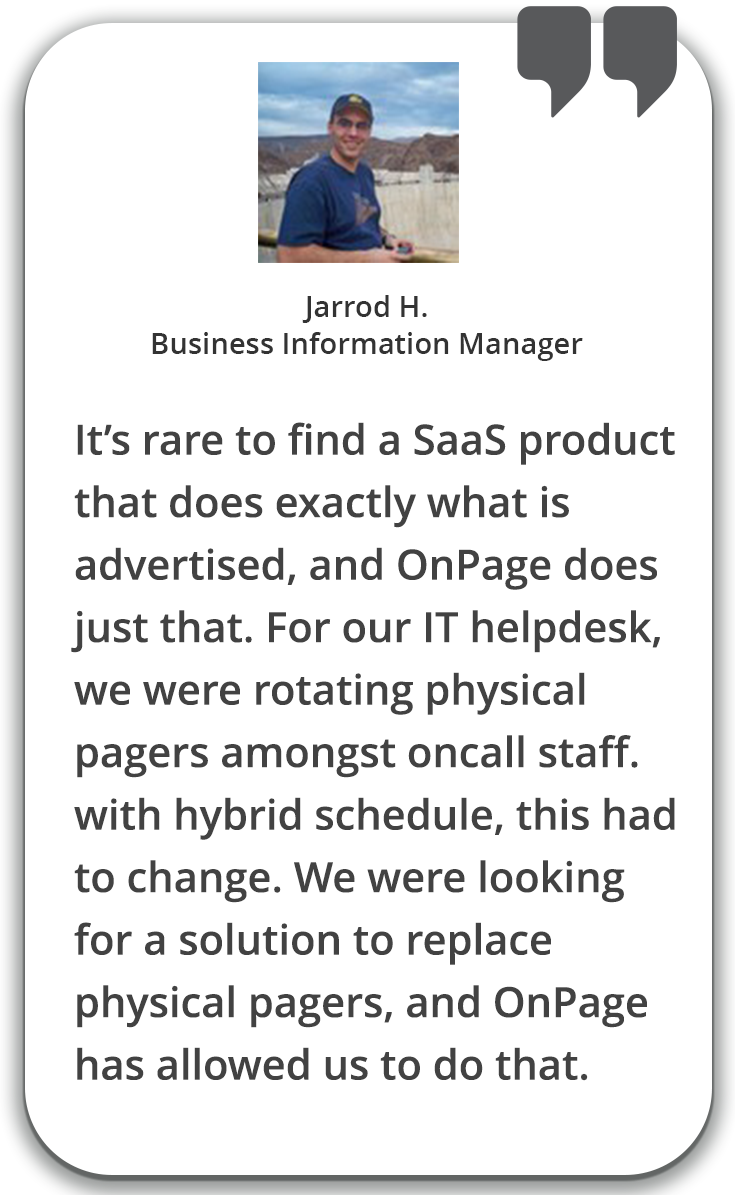
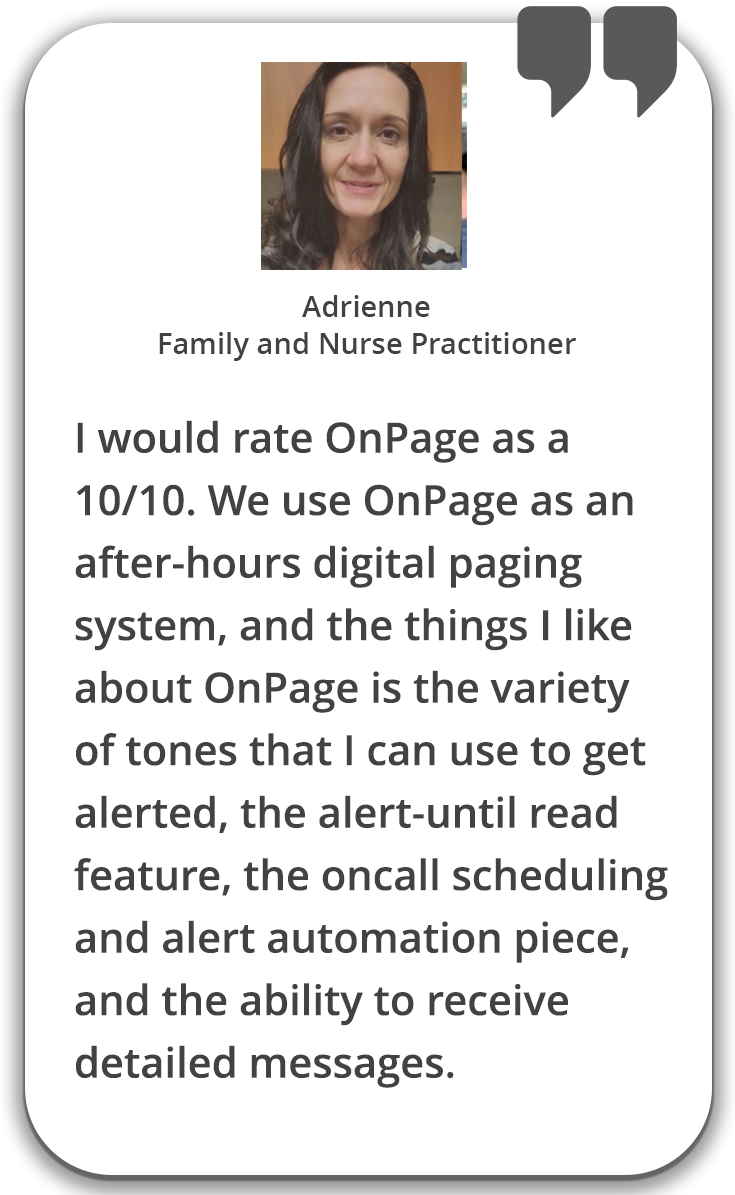
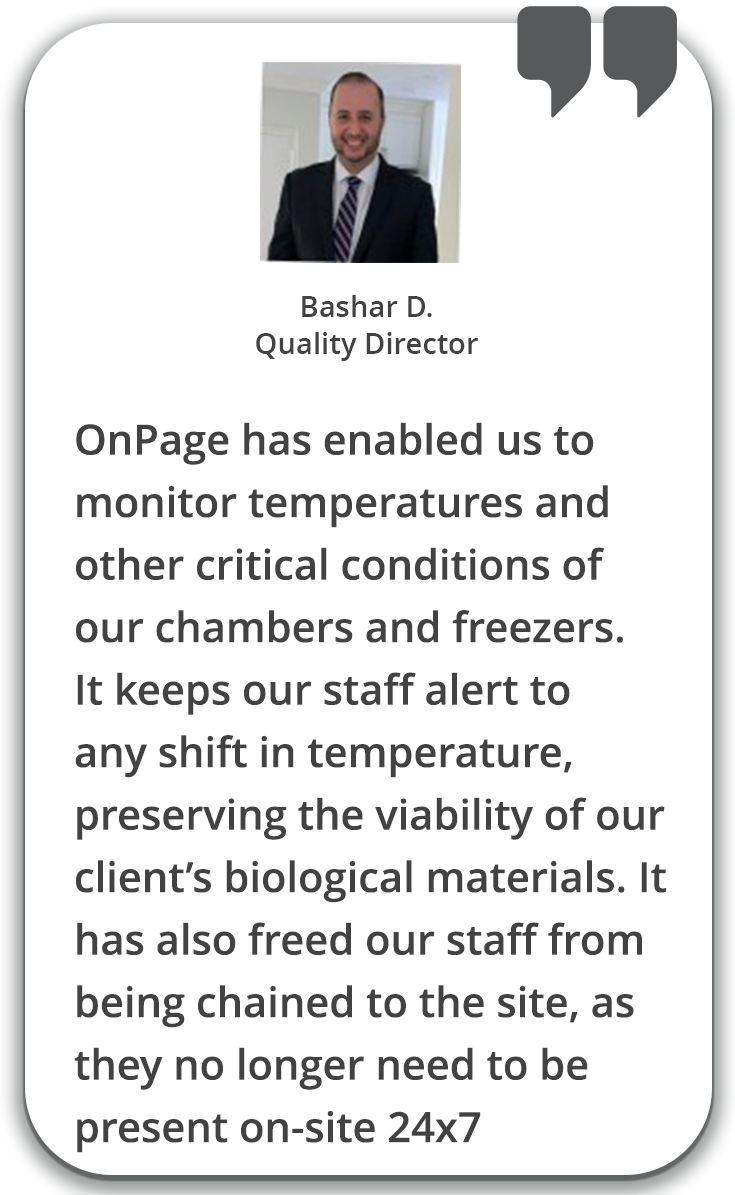
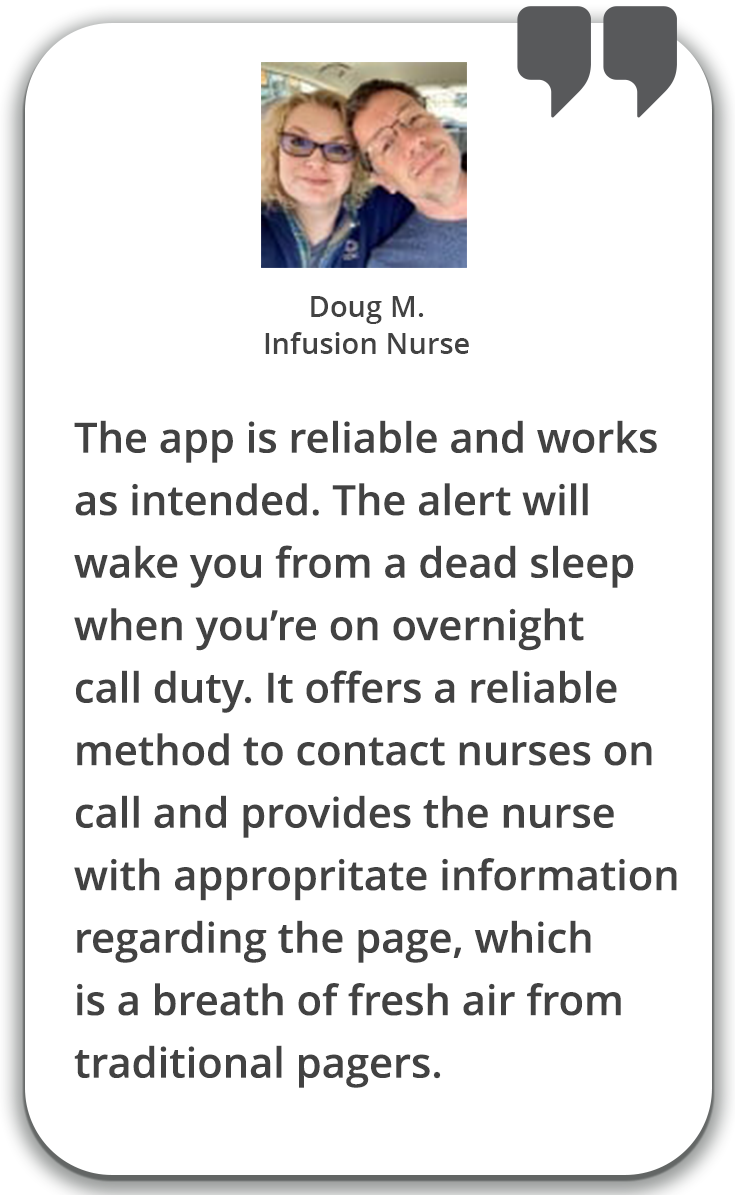
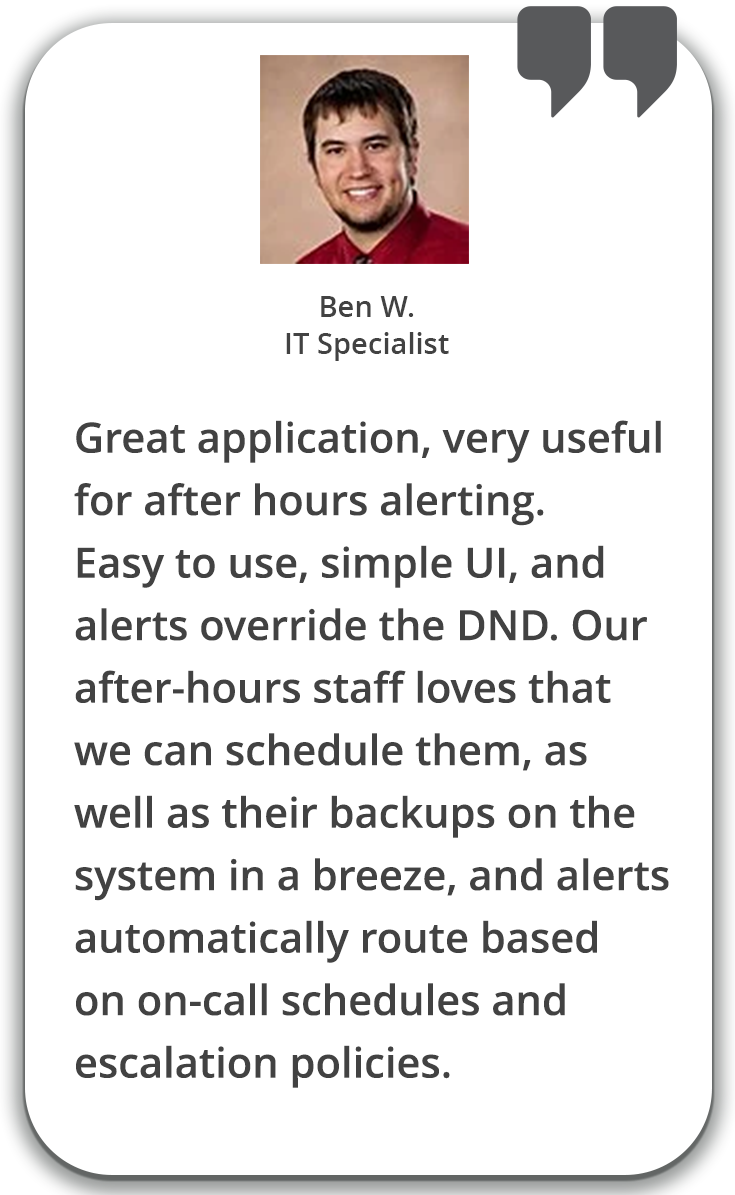

Elevate critical alerts. Bypass phone’s DND settings and alert persistently until read.

Gain flexible, fail-safe scheduling capabilities. Set up on-call rotations and escalation rules.

Enable direct access to your on-call staff via live call, voicemail, or SMS over a dedicated number.

Analyze incident response time with real-time reporting. Uncover trends to optimize workflows.

Escalate alerts when a member is unavailable. Add several channels of communication for redundancy.

Drive business continuity with mass notifications. Blast messages at scale during crisis.