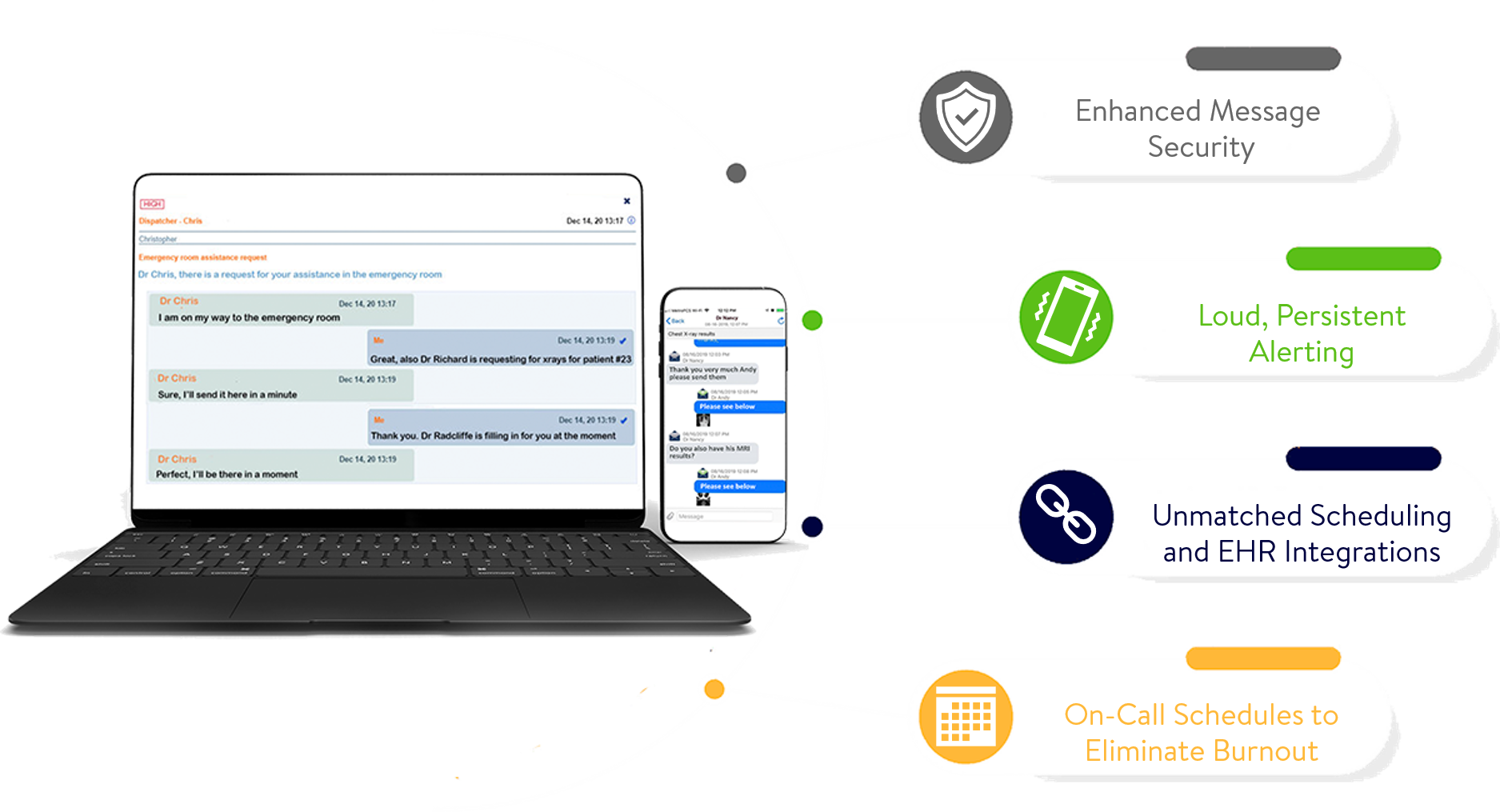
Decreased Costs and Improved Efficiency
According to the Ponemon Institute, the use of traditional pagers in a healthcare setting adds costs and prolongs patient care. Research shows that pagers cost the healthcare industry an additional $11 billion per year.
These costs are the result of pagers causing delays in providing patient care as well as in wasted time from using pagers to coordinate care. Waiting to get access to the right doctor and exchanging the correct information are some consequences of using pagers.
Patient Benefits
According to a study by the University of Pennsylvania, “Patients whose hospital care providers used mobile secure text messaging as a means of communication had shorter lengths of stay compared to patients whose providers used the standard paging system to communicate.”
Physician Benefits
Physicians that prefer to exchange emails rather than send text messages face increasing scrutiny of their communication methods, guiding them to use HIPAA-secure messaging with greater frequency to ensure that any PHI is encrypted and secure.
HIPAA-compliant messaging applications ensure message accountability and eliminate the need for physicians to play “phone tag.” This means that physicians can spend less time trying to reach colleagues and wait for responses. Instead, they get quick responses to their texts and can better focus on their patients.
Nursing Benefits
Nursing units benefit from faster, more complete responses from physicians and other colleagues. For example, a nurse needs a second opinion on an electrocardiogram (EKG). With HIPAA-secure messaging, he can immediately forward the image of the EKG to a colleague along with comments. Because messages sent via the app get attention, he can rest assured that the message does not get lost in a full inbox or among dozens of voicemail messages. For better accountability and peace of mind, he can see when the message is read.
Nurses can also accelerate care delivery and get more accurate diagnoses by transmitting photos in a secure and encrypted manner to the consulting physician.