WHAT IS ONPAGE
Rise Above the Clutter®
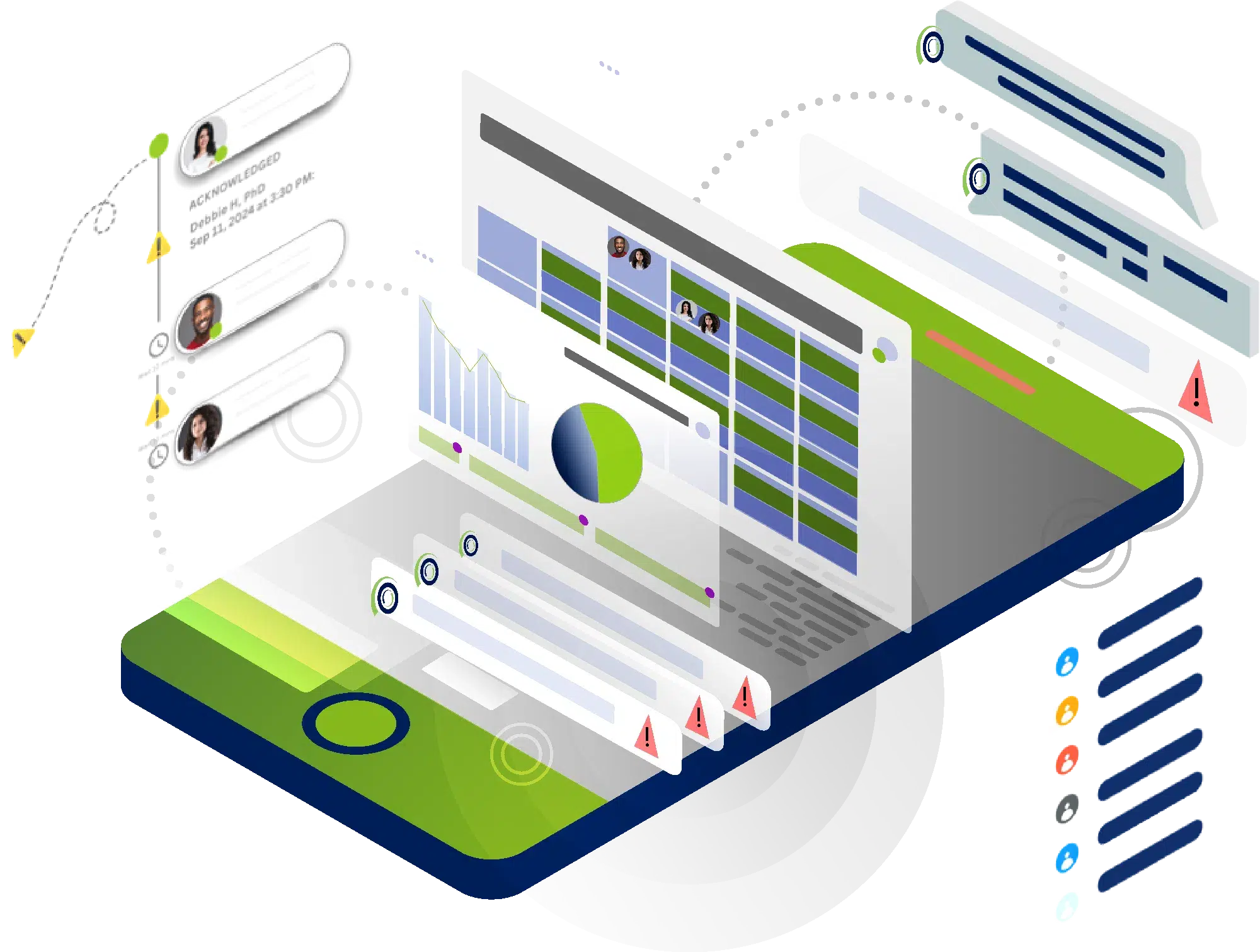
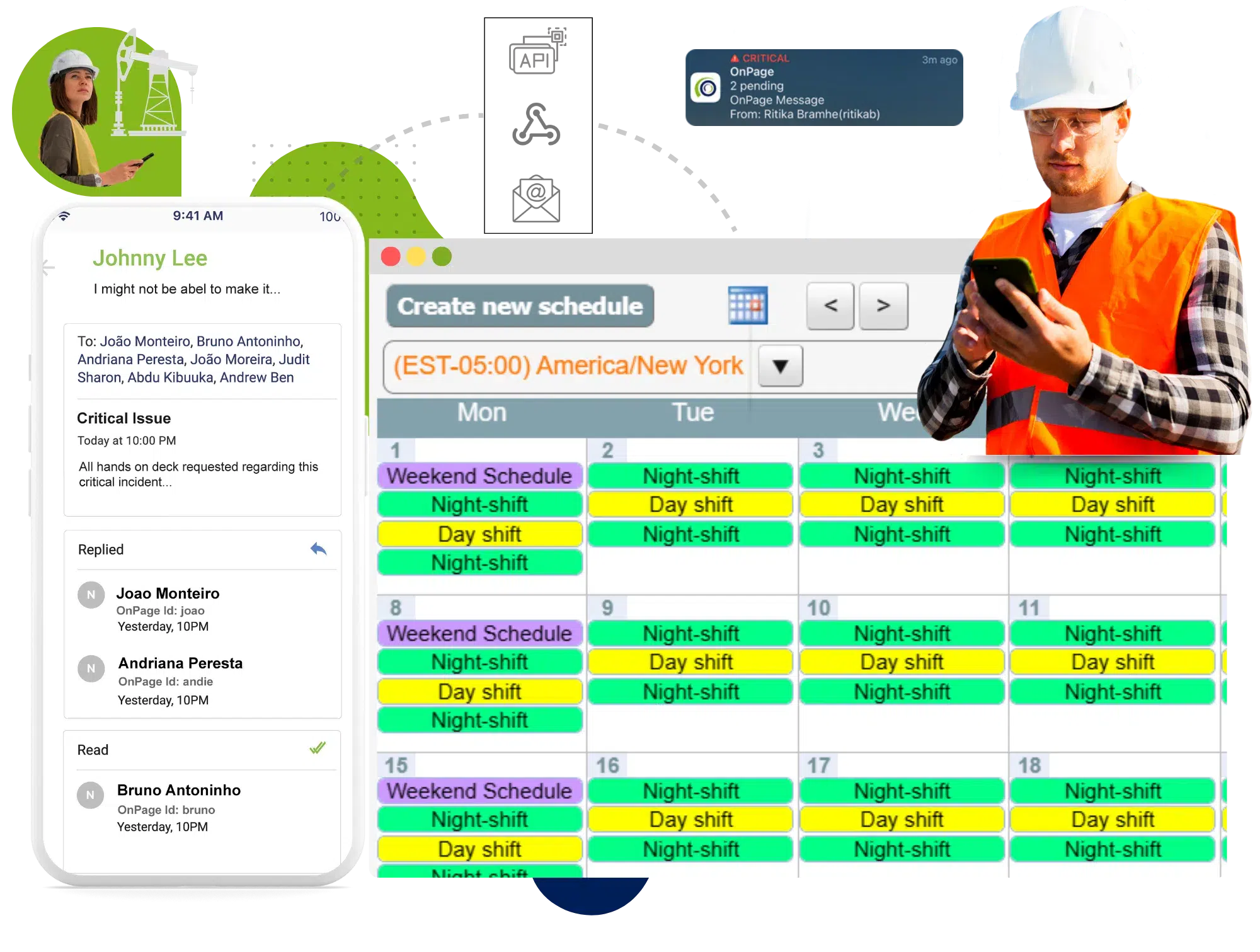
In today’s digital landscape, where notifications from countless tools and systems compete for attention, OnPage ensures that critical alerts rise above the noise.
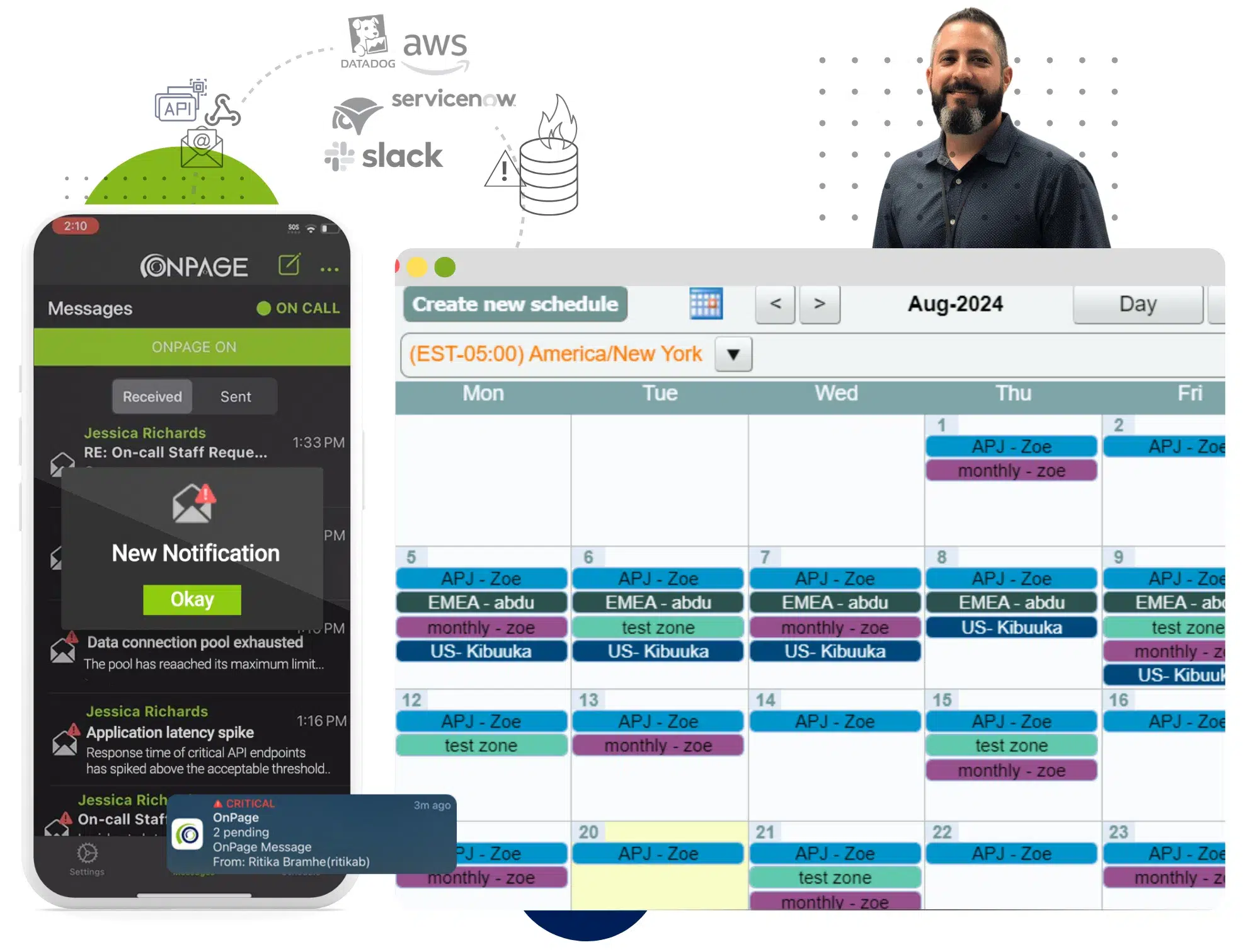
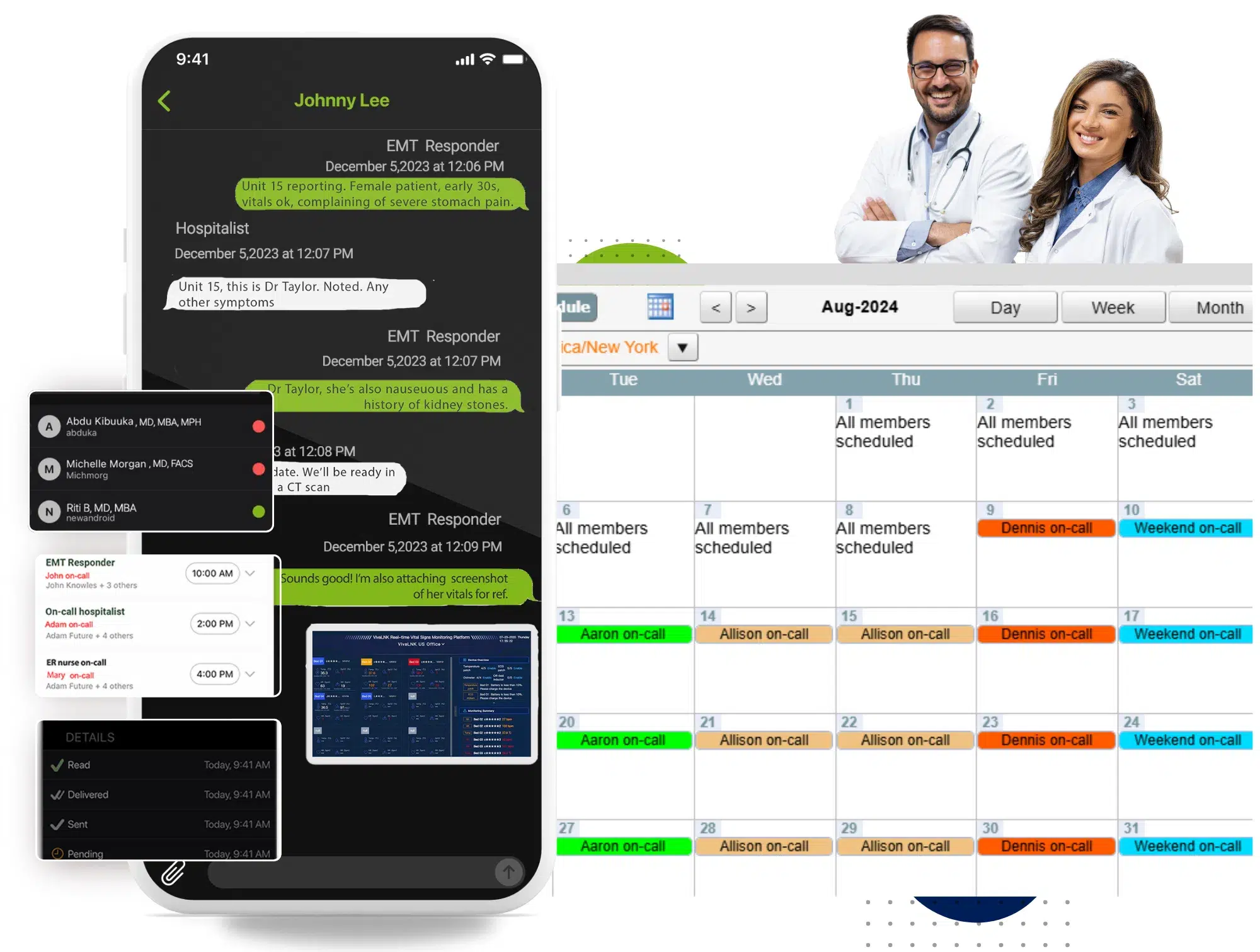
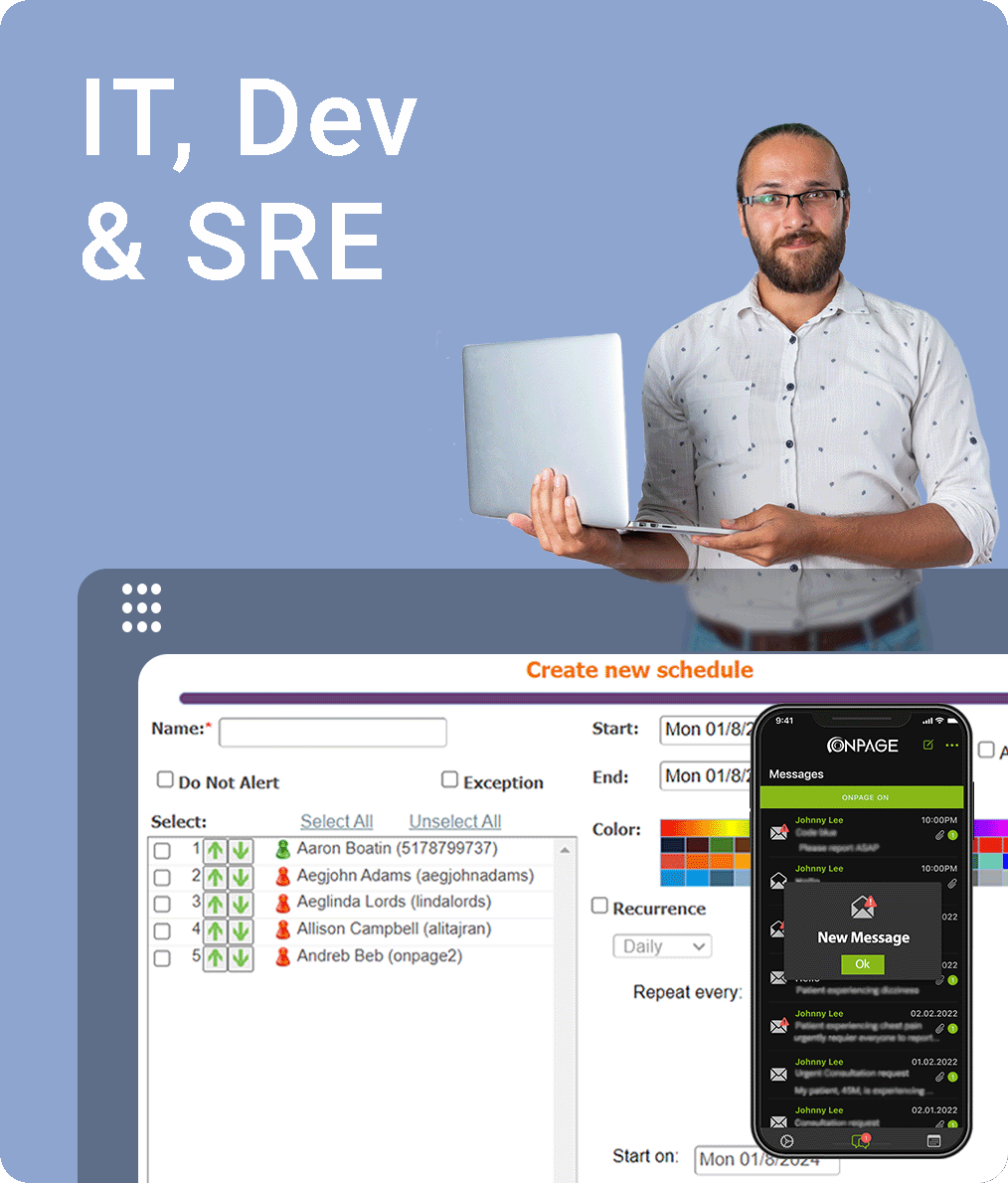
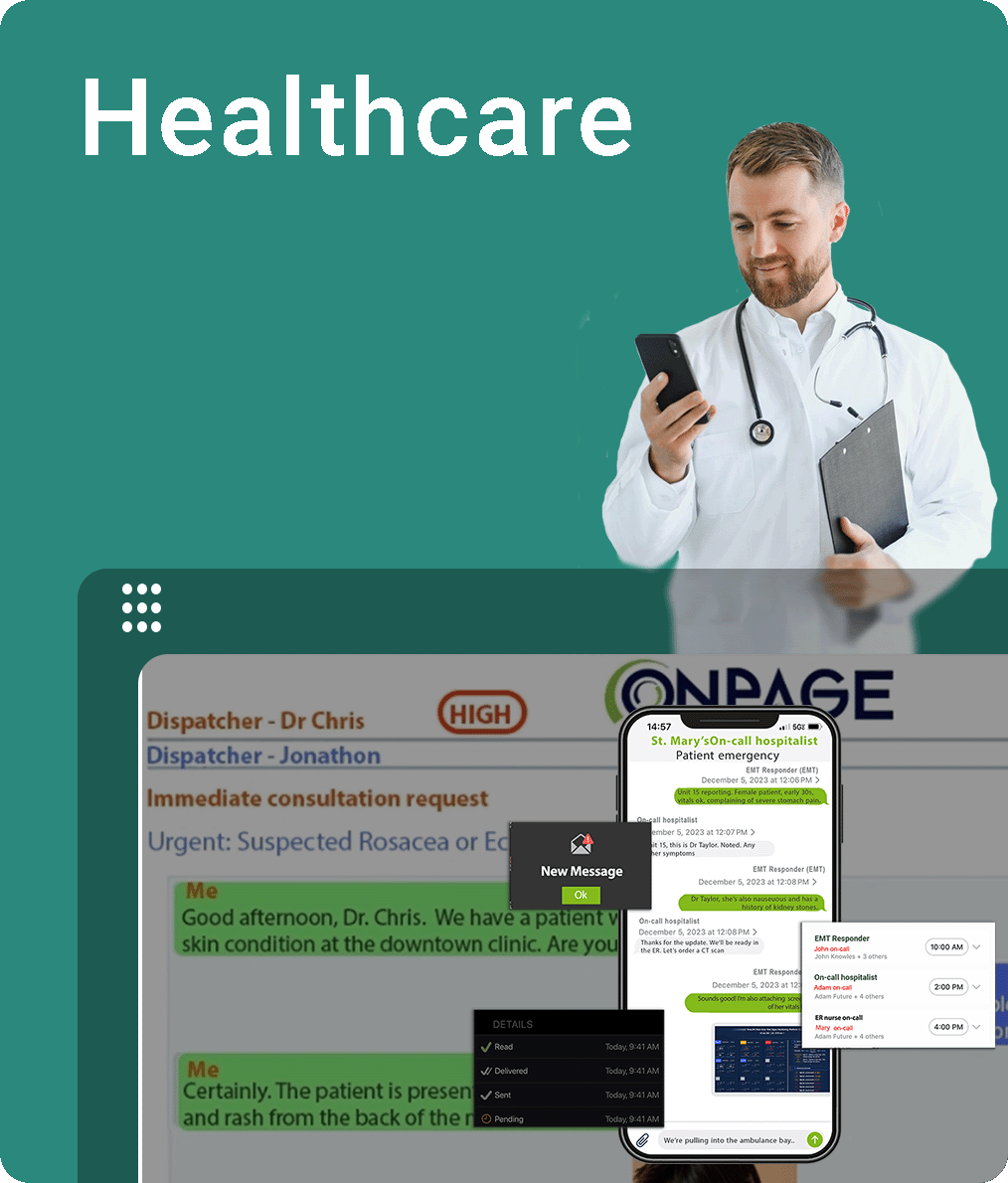
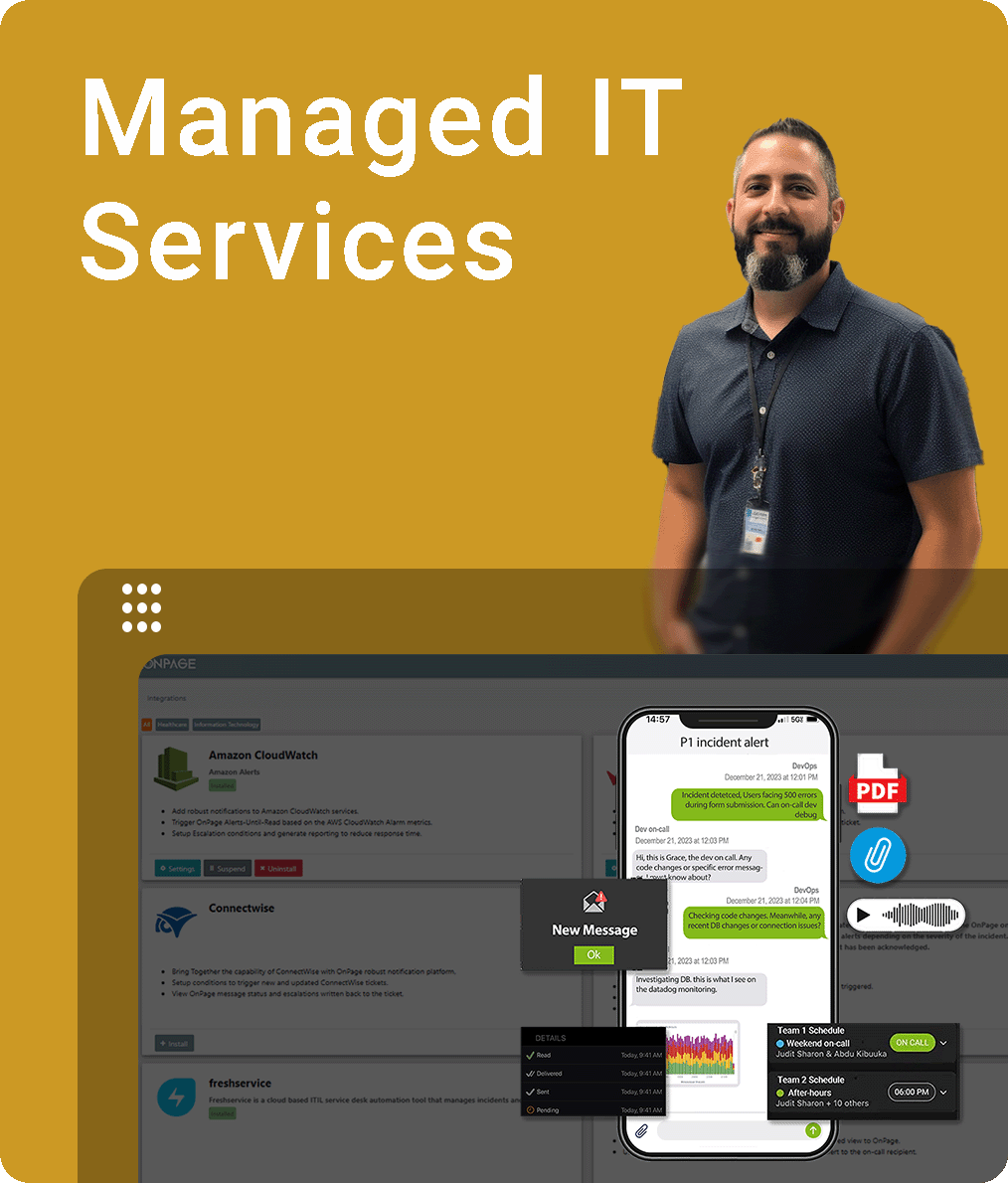
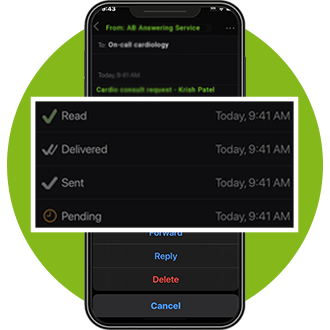
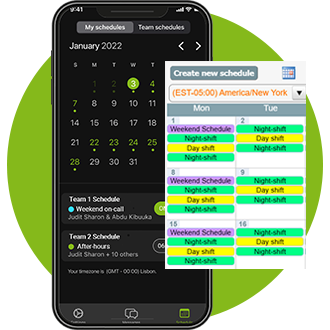
Whether a life-saving notification regarding patient health or a critical issue with your tech systems, OnPage routes high-priority notifications with unmatched precision and reliability, based on schedules and a rule-based engine.
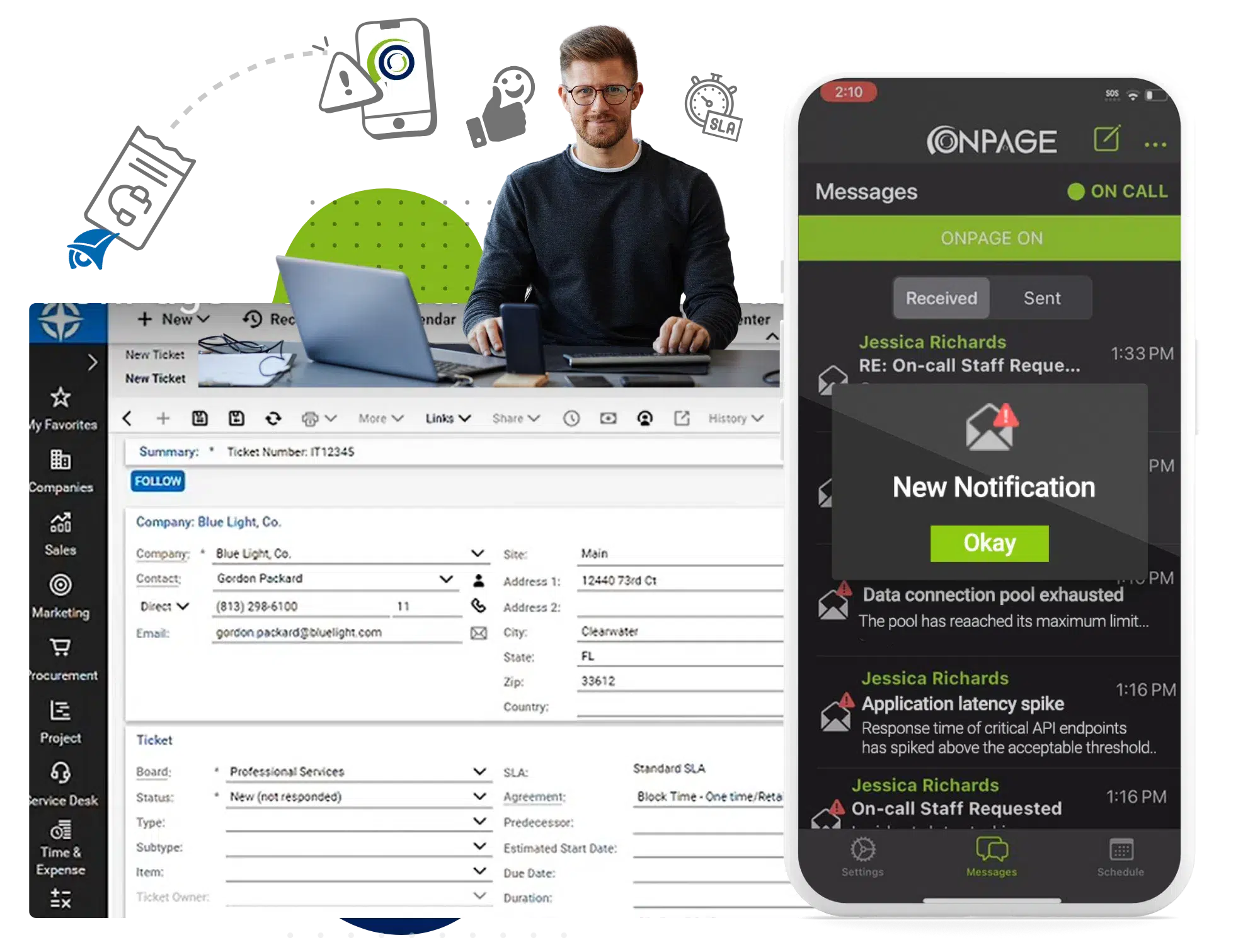
Our platform keeps your on-call team connected and ready to respond, offering a secure, dedicated space for seamless collaboration. Plus, it easily integrates with the systems you already use.
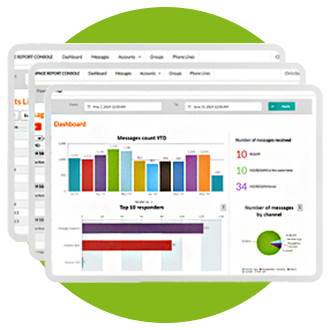
With OnPage, your team can quickly, securely, and efficiently tackle urgent issues.