Blog

Cloud Cost Incidents: Catching Cost Calamities on Time
What Is Cloud Cost Management? Cloud cost management, also referred to as cloud cost optimization, is the process of managing and controlling a company’s spending on cloud services. This can be achieved through a variety of methods, such as usage monitoring, resource optimization, and cost forecasting. The first step in managing cloud costs is to … Continued
read more
Top 3 experiences we are looking forward to at HIMSS24!
The OnPage team is thrilled to announce that we will be attending HIMSS24! As we prepare for the conference, we find ourselves getting more and more excited to go…and no, not just because we get to escape the cold up here in Boston for a few days. But because we get to connect with a … Continued
read more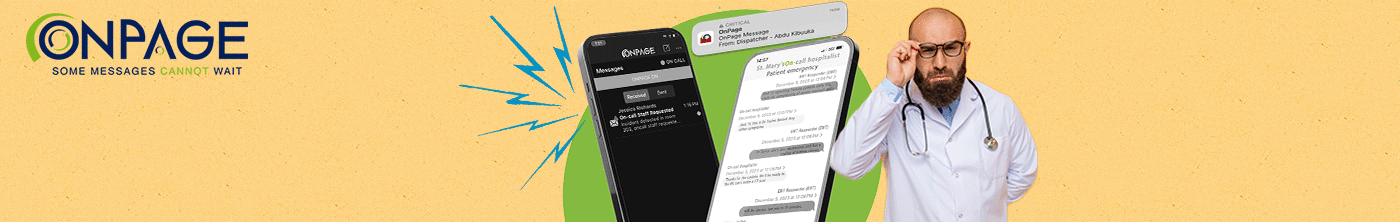
Navigating the Transition to Secure Texting
The Pager Predicament Recently, I stumbled upon an eye-opening NPR podcast that delved into the lingering use of pagers in healthcare—a seemingly outdated technology that continues to drive communication in hospitals. As I listened through the debate around its persistence, discussing challenges and unexpected benefits, it prompted reflections on facilitating a seamless shift to secure … Continued
read more
On-Call Software Engineer Roles and Responsibilities
What do software engineers do during on-call? Most software engineers know that they are typically tasked with on-call shifts, but new software engineers entering the field may be asking themselves – What do I even do if I get scheduled for an on-call shift? This is a common question that often doesn’t get answered until … Continued
read more
LLM Monitoring and Observability
What is LLM Large Language Models (LLMs) are advanced artificial intelligence models designed to comprehend and generate human-like language. With millions or even billions of parameters, these models, like GPT-3, excel in natural language processing, understanding context, and generating coherent and contextually relevant text across various applications. What is LLM Observability and Monitoring? LLM observability … Continued
read more
Managing Databases on AWS: A Practical Guide
What Are AWS Databases? Amazon Web Services (AWS) provides a range of managed database services that provide multiple database technologies to handle various use cases. They are designed to free businesses from tasks like database administration, maintenance, upgrades, and backup. AWS databases come in several types to cater to different business needs. These include relational … Continued
read more
Best Practices to Avoid Website Outages on Black Friday
The most frenzied shopping day of the year – Black Friday – is fast approaching, and businesses around the globe are bracing themselves. However, imagine this – a massive number of eager shoppers ready to snag the hottest deal, and just when your website should be working at its best, it crashes, leaving behind frustrated … Continued
read more
What is Vulnerability Management?
Vulnerability management is a critical aspect of a cybersecurity strategy. It refers to the systematic and ongoing process of identifying, classifying, prioritizing, and addressing security vulnerabilities in a network environment. This proactive approach to network security aims to minimize the risk of exploitation by attackers. Vulnerability management is about staying one step ahead of potential … Continued
read more
OnPage Releases Healthcare-Focused Slack Integration
Introduction In the healthcare realm, the need for communication platforms that meet HIPAA standards is undeniable. Enter Slack, a popular collaboration platform armed with robust security features. However, the real game-changer emerges through the integration with OnPage. This isn’t just an upgrade in collaboration; it’s a transformative shift in critical communication within healthcare—a field where … Continued
read more
The Journey Into Automation: Optimizing Care Delivery
Automation as the foundation for optimizing care delivery In a world where efficiency and precision are the cornerstones of progress, automation has become the unsung hero across diverse industries. From manufacturing floors to customer service, its transformative power has reshaped the way we work and deliver services. Within the healthcare sector, automation has left no … Continued
read more