How do I ensure BYOD security in healthcare?

At OnPage, we often see healthcare administrators pushing back against the use of personal smartphones. Administrators believe that enabling bring-your-own-device (BYOD) presents a security threat in healthcare. Indeed, BYOD security in healthcare is challenging and leads to many questions. For example, many hospital administrators wonder how they can ensure that ePHI is not intercepted and used for nefarious purposes? How can hospitals ensure communications don’t violate patient privacy? How do they ensure the security of messages sent through BYOD?
These concerns and other similar ones were highlighted by the Office of Civil Rights (OCR) in their recent report on Mobile Devices and Protected Health Information. According to the OCR :
Entities regulated by the HIPAA Privacy, Security, and Breach Notification Rules (the HIPAA Rules) must be sure to include mobile devices in their enterprise-wide risk analysis and take action(s) to reduce risks identified with the use of mobile devices to a reasonable and appropriate level
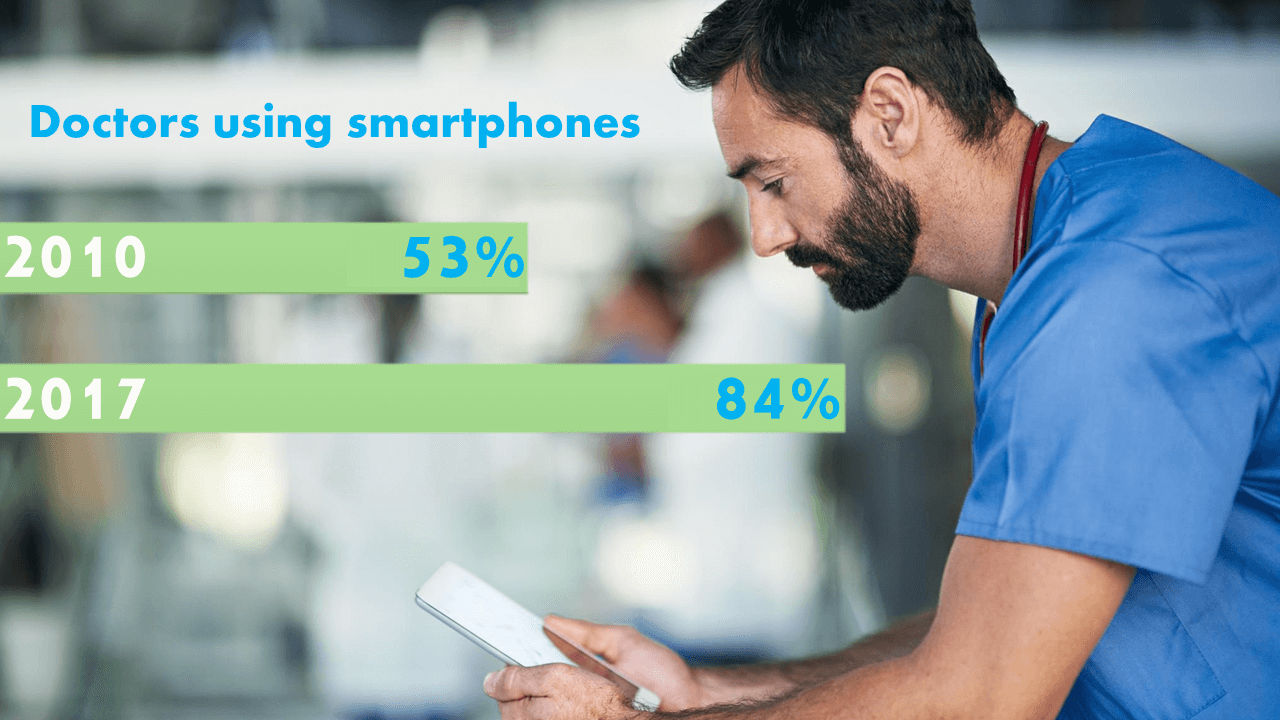
Benefits of BYOD in healthcare
BYOD benefits healthcare because they provide a way for physicians to be available to their patients. Additionally, it is how much information is exchanged between and among practitioners. What administrators need to focus on is making sure the information is exchanged in a secure, encrypted and HIPAA-compliant manner.
BYOD in healthcare is also important because -it acknowledges the fact that people are going to bring their own device and seek to use them in their work, as well as their personal life. Furthermore, healthcare providers can’t really afford to give a smartphone to everyone who would benefit from the device.
Don’t blame BYOD
The real culprit in BYOD is not the use of the device but poor mobile hygiene. Often the mobile devices being used lack encryption or suffer from poor password management. In addition, employees have a tendency to leave their mobile device vulnerable such as forgetting them on the backseat of a car or on a desk or in a coffee shop or in other vulnerable locations. In these instances, the devices are often the object of theft. At this point, the issue is no longer BYOD.
This vulnerability was further highlighted by the OCR report when it pointed out that:
Due to their small size and portability, mobile devices are at a greater risk of being lost or stolen. A lost or stolen mobile device containing unsecured ePHI can lead to a breach of that ePHI which could trigger HIPAA breach notification obligations for a HIPAA covered entity or its business associate.
We can see then that the issue is more one of how to ensure appropriate steps are taken if devices are stolen. The issue is not whether practitioners can bring devices to the hospital as even a work provided smartphone is vulnerable to theft. Instead, administrators need to focus on how to ensure the security of the ePHI and related patient information on smartphones.
What steps administrators can take to ensure BYOD security in healthcare
The real issue boils down to one of maintaining BYOD security in healthcare. To ensure security, healthcare organizations need to react swiftly to the news of lost devices. They need to have a plan or checklist they follow. By minimizing the time between the actual loss or theft of the device and apprising appropriate officials, healthcare organizations can minimize the impact of the loss. Ideally, practitioners will be using applications like OnPage on their smartphones that enable remote wipe so that any information that had been on the smartphone is erased.
Additionally, administrators need to make sure that HIPAA guidelines govern all mobile devices used at the hospital or clinic. HIPAA doesn’t just mean securing your desktop computers and servers. It also means that smartphone communications on applications are secure, encrypted and require sign-in.
Lastly, administrators need to make sure they provide staff with defined training and procedures to follow if their smartphone is lost or stolen. Who should a doctor or healthcare officials contact at the hospital or clinic? When IT officials have been contacted about the loss, what procedures should they follow? It is extremely important to identify roles and responsibilities within the organization and what must be done by whom when theft is suspected.
Conclusion
The demand for BYOD is increasing and organizations are faced with pressure to allow BYOD. However, organizations need to be careful to ensure that communications regarding patients are encrypted and meet the mandates of HIPAA requirements. By using remote wipe policies, password protection and a defined action plan it becomes much easier to maintain the health of mobile devices and ensure BYOD security in hospitals.
Interested in learning more about BYOD security in healthcare? Read our whitepaper on Smart Doctors Use Smartphones




